Our Product
The Posturity Oversight Service
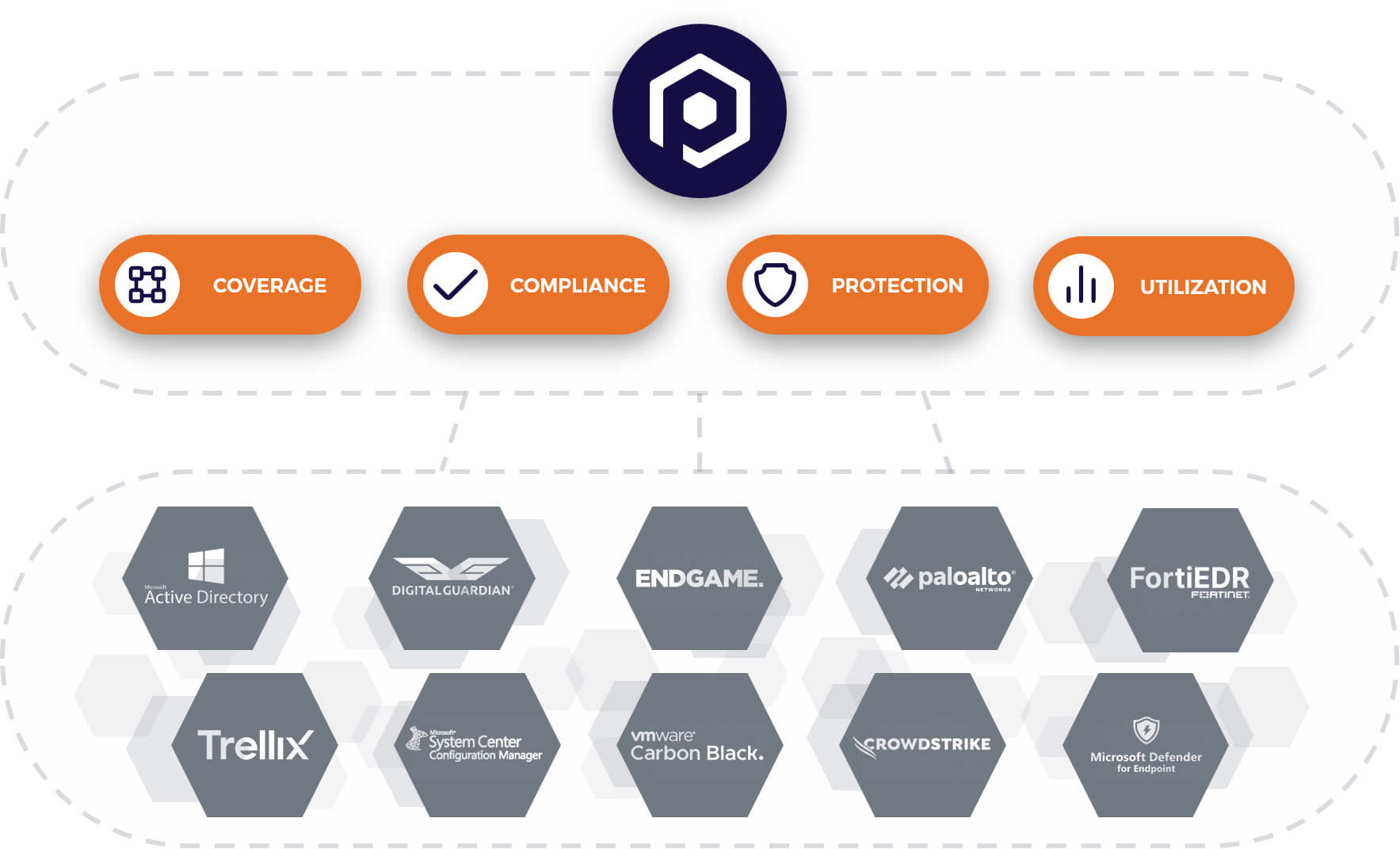
The Posturity Oversight service gives security teams the ability to define, execute, govern and continuously improve their cybersecurity technology stack. Delivered as a managed technology governance service, the Posturity Oversight service translates your strategy into action by connecting with your core security tools and delivering the necessary insights and actions to achieve your goals.
What are our customers saying?
Posturity is a key tool in determining if my endpoints have the security capabilities coverage they need to protect against the latest and most prevalent cyberattacks. It also helps me to direct my limited resources towards resolving the highest risk exposures first.
CYBER THREAT LEADER

Why Posturity?
1 Get what you expect from your security stack
The average tool stack is full of overlapping capabilities, uninstalled tools, underutilized licenses, and critical protection and compliance gaps. Posturity gives you the continuous visibility, control, and actions to address all these challenges.
2 Consolidate and rationalize your stack with confidence and speed
With the average number of security tools in an enterprise environment at 45 there is an obvious need for consolidation. The challenge is how to do this in a secure, timely, and objective manner. Posturity solves this challenge by measuring the actual operating performance and the MITRE protection capabilities of your tool stack enabling a timely data-driven decision.
3 Automate your security technology strategy
Communicating, implementing, monitoring, and updating your cybersecurity technology strategy is increasingly difficult. Posturity addresses this by translating your strategy into an operational ready “blueprint” that can be monitored and continuously improved towards a state of optimization.
Who Uses Posturity?
Security Leadership
Constant change from “High-Delta environments” drives the size and complexity of the security stack resulting in overspend, more IT risk, and a disconnect with the operation teams responsible for deploying it. Posturity provides the oversight to make sure security tools are deployed, available, and optimized.
IT & Security Operations
IT and security operations teams struggle to keep up with the ever-changing deployment requirements of security tools in an expanding sprawl of devices, cloud services and tools to secure them. The result is a constant and tedious manual effort of finding and securing devices. Posturity provides operations team with an always up-to-date and unified device inventory and the prioritized actions required to meet enterprise goals.